Key Takeaways
It seems as though data, privacy and cybersecurity are topics that never drop out of the news cycle. From the Facebook & Cambridge Analytica scandal to the 97th “we’ve updated our privacy policy” email you’ve received in the advent of the EU’s GDPR coming into effect.

In addition, the Equifax Breach last year still has a few more surprises up its sleeve. In March they announced that a further 2.4 million more consumers were affected (than the previously reported 145 million). Cybersecurity has never been more important which is why we thought we’d highlight some of the findings of the 2018 Verizon Data Breach report. For the past 11 years Verizon Enterprise Solutions have released a report that details real-world security incidents, data breaches, and the trends behind them.
Here are 5 takeaways we think every business should be aware of:
1. Ransomware is on the rise
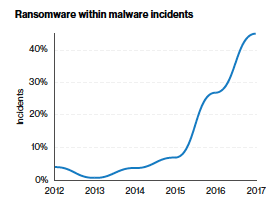
Ransomware is a form of malware which locks down the afflicted computer and demands payment to unlock it, typically via a cryptocurrency such as bitcoin. The malware encrypts the infected system rendering it (and it’s data) completely unusable. Verizon report that 56% of malware incidents involved ransomware making it the most prevalent form of malware. What’s more concerning is that hackers are turning their attention to critical systems such as servers rather than employee devices.
Remember earlier this year when the city of Atlanta was hit by a cyber attack? Details about the attack are hard to come by (City officials remain tight-lipped) but reportedly hackers are demanding $52k to unlock the infected computers. According to news outlets, residents could not pay their water bill or their parking tickets. Police and other employees had to write out their reports by hand. The costs to recover from the attack have been estimated at over $2.6m.
2. Social attacks are not going away
We recently wrote a post detailing the common forms of social engineering, a method by which hackers use psychology to trick victims into giving out sensitive information like usernames and passwords.
Companies are three times more likely to get breached by social attacks versus vulnerabilities in their security systems, so educating employees about cybersecurity should be a priority. You may think oh, I would never fall for a fake email from supplier asking for payment but you’d be surprised. Verizon found that phishing and pretexting represent 98% of social incidents and 93% of breaches.
We’ve seen examples of this firsthand; one of our clients was subject to a phishing scam whereby multiple payments were made under what the employes thought were the CEO’s instructions. They were actually prompted by fraudulent email addresses, and losses totaled close to $200,000.
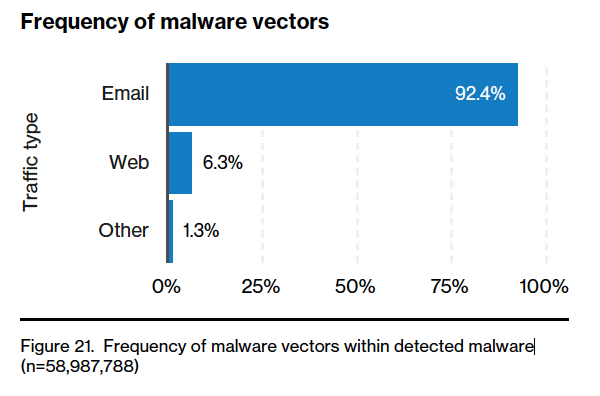
3. Email is a gateway
As illustrated by the phishing example, email continues to be a go-to access point for hackers. For good reason, the barrier to entry is low, hackers can automate emails en masse and all it takes is one bite to get access to an entire organization. The stats back it up too:
- Email was the entry point in 96% of social attacks
- 49% of non-POS malware was installed via malicious email
In the breaches they investigated featuring a social engineering component, 70% involved phishing and 20% involved pretexting. Pretexting, also covered in the aforementioned post, is similar to phishing but involves a lot more research and staking out on the hackers part. They target a specific individual using information they’ve learned about them. For example, a bank scammer pretending to be an employee of another branch and asking for login credentials.
4. Why are there so many DDoS attacks?
Verizon recorded a whopping 21,409 Distributed Denial of Services incidents, almost 40% of all incidents. DDoS attacks basically involve a network of botnets that floods a server with more requests than it can handle causing it to crash or become inaccessible. However, businesses shouldn’t be overly concerned about the number of DDoS attacks but rather what the intent behind them is. Sure, downtime can be a real issue, but most companies that do suffer a DDoS normally aren’t under attack that long each year. The median is three days.
However, misdirection is the name of the game here. DoS attacks are often paired with more harmful attacks that result in data breaches of PII (personally identifiable information) or financial information. Hackers hope your attention on trying to keep services up and running, will cause you be distracted from their true intentions of carrying out an attack elsewhere on the network.
5. Small businesses are at risk
Only large enterprises should worry about cyber attacks or data breaches right? Nope, in fact, over 58% of security breaches happened to small businesses. Criminals understand that large companies are pouring significant piles of cash into beefing up their cybersecurity (Gartner, forecasts worldwide enterprise security spending to total $96.3 billion in 2018). So naturally, SMB’s become a logical target.
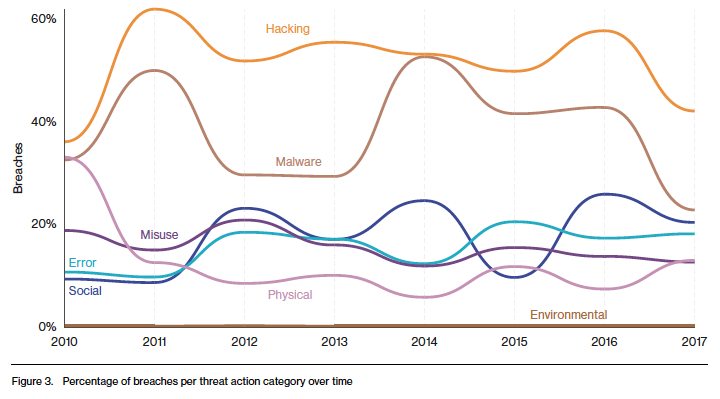
Hackers have a number of tactics in their armory to target small business some of which we’ve touched on. Here’s how the primary tactics have varied over the past few years:
Financial gain is unsurprisingly, the primary motivation behind 90% of data breaches and gaining access to credentials is the driving force whether it’s by malware, phishing, brute force, keylogging or physical theft.
How do I protect my business from data breaches?
While these findings can seem a little daunting, especially if you are running an early stage tech startup there are few actions you can take to limit risks from cyber attacks and data breaches (FYI this is a broad overview and each should be considered in detail):
-
- Data Security & Encryption – A good place to start is to make sure that any personally identifiable information (PII) you manage is encrypted and figure out where the gaps in your cybersecurity are. You can’t secure everything so pick your battles wisely.
- Training – the human factor is very much at play. Take time to educate your employees about the danger of social attacks and what they need to on the lookout for. A Security Awareness Program is one of the best ways you can protect your company from the dangers of social engineering. The program educates your employees on the dangers of social engineering, the importance of data and how to respond when they suspect an attack.
- Insurance – hackers are smart and some things may be out of your control. That’s where insurance comes in to play. Putting a Cyber Liability policy or Tech E&O policy in place can be an invaluable backstop for when your best efforts come up short and data is compromised.
To learn more, you can always reach out to a member of our team by phone 646.854.1058 or email info@foundershield.com at any time. Or create an account here to get a quote for a comprehensive program that protects you from the data breaches and cyber attacks we’ve discussed!