This post was originally featured on the OpenView blog here. OpenView is an expansion stage venture firm that helps build software companies into market leaders.
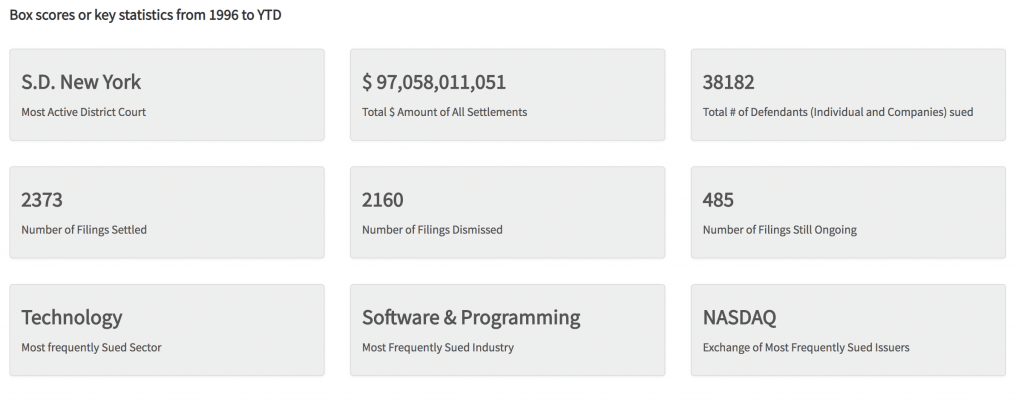
Did you know that the tech industry is the most frequently sued sector, with software and programming being the most sued industry?
With the entire service model, and thus profit, dependent on uptime and service availability, the tolerance for service interruption is minuscule. When Slack went down for a couple of hours in June, all of our hearts skipped a beat. (You have to feel for their support team dealing with the onslaught of 30k+ tweets). Moreover, the amount of sensitive data a SaaS organization keeps can climb into millions of records for a large company.
SaaS companies commonly face risks having to do with service interruption or data breach events.
Let’s talk about cyber attacks first. A SaaS company, big or small, remains a major target for cybercriminals. SaaS products are available 24/7 and their systems store all kinds of sensitive data which means that social engineering and data breaches are as common as they are effective.
Since a SaaS company relies heavily on its ability to deliver uninterrupted service to the customer, a system failure (or worse, a repeated system failure) can be crippling. Whether a hardware issue, a scalability problem or loss of power, it’s essential to prepare countermeasures to deal with these situations.
As your company grows, the risk factors increase. You have a bigger target on your back both from cyber attack and service uptime standpoints.
1. Operations & Loss Control
It’s obvious that limiting your liability and keeping your profit margin intact is incredibly important for any SaaS company. The operations department is vital to ensuring that your service runs smoothly. The team should also implement countermeasures and controls to mitigate and minimize the risks we discussed above.
Administrative Controls
When we talk about administrative controls, we refer to contracts, internal procedures and documenting processes.
Essential countermeasures include implementing an on-call rotation for the operations team, ongoing documentation about the applications, a playbook of step-by-step directions to known problem resolution, disaster recovery plans, and business continuity planning.
You’ll be able to quickly and efficiently react to a problem with these policies in place.
Technical Controls
Administrative controls are useless without the technical controls. They keep downtime to a minimum while increasing your ability to quickly deal with issues as they arise.
The industry gold standard for a SaaS service availability is 99.99% uptime. This gives you 5.26 minutes of downtime per year. While a 99.99% uptime is rarely achieved, your SLAs specify the absolute minimum that you are committing to.
So how do you reduce your total downtime? What are the strategies that companies big and small implement to stay at the top of their game?
- Alerting and metrics: This control goes hand in hand with an on-call rotation we mentioned earlier. The alerting system (biggest players in the industry include CloudWatch, PagerDuty and Nagios) will notify the on-call team member of any possible issues. You can’t effectively figure out what the issue is without good metrics. They’re invaluable in determining the root cause of the problem.
- Centralized logging: Centralized logging allows you to collect logs of everything that transpires in the system. Along with metrics, centralized logging helps establish the root cause of a problem. It also allows you to document the timeline of the steps taken to resolve the issue and what other countermeasures can be taken to avoid similar problems in the future.
- Redundancy: When designing your network system, pay particular attention to the redundancy of your systems. When an issue arises, it is vital to be able to continue your service seamlessly. The most common choices are load balancers, redundant databases, and redundant servers so there is no impact to customers when the primary servers go down.
Another option is to use cloud providers for PaaS solutions like Elastic Beanstalk and Digital Ocean. PaaS provides a platform allowing you to host, design and manage your applications in the cloud. It also includes redundancy controls, so you do not need to design them yourself. However, PaaS becomes less cost-effective as your company scales up.
In short, it’s essential to design a system that includes redundancies and failovers to avoid impact to customers. In many cases, your SLA will dictate how many layers of redundancies you really need to have.
Laws & Compliance
Time to talk GDPR, the European Union’s new privacy legislation. It includes how and to whom breach notifications should be made and sets forth the “right to forget” principle whereby every European consumer has the ability to access and delete their private information.
So, does this impact US-based businesses? Absolutely! The legislation applies to any organization that does business with a European citizen. If a European citizen purchased something from you or even just subscribed to your newsletter you are required to comply with GDPR.
The US has also enacted multiples laws that deal with privacy and data breaches. Ensuring compliance, especially for a company that primarily services customers, is critical.
2. Cybersecurity
Cybersecurity is a widely discussed topic given recent data breach scandals involving giants such as Equifax and MyFitnessPal. These events serve as a constant reminder that cybersecurity can make or break your company.
- Firewalls prevent unauthorized network traffic from reaching network services. Experts recommend auditing, managing, and updating your firewall rules at least quarterly or even more often depending on your business needs. It’s wise to implement firewall log reviews as a part of your alerting and monitoring process. In the context of an audit of insurance companies, ensuring robust firewall management is crucial to safeguarding sensitive customer data and maintaining regulatory compliance.
- 2-Factor Authentication gives you a second way to verify user’s identity and their permissions before allowing access to sensitive data. This two-pronged approach requires two pieces of data from the user – “something you have” (e.g. FOB with a current key or Google Authenticator key) and “something you know” (e.g. password).
- Backups – the key to this security measure is designing solid backup solutions and testing them often. There is nothing worse than losing your data and being unable to recover from the backup. A faulty backup can corrupt data or damage media. A backup system and testing procedure will uncover these issues.
- A security awareness program is an essential component to reducing social engineering risks for your employees and thus improving your cybersecurity. With a security awareness program, you create a company culture where critical security questions are asked, and procedures are put in place to mitigate risks.
The training helps your employees to identify social engineering attempts and provides a reporting structure indicating who to contact when you suspect a security breach. Depending on the size of your organization, you can do an online security training from a reputable company or hire an outside consultant to develop the program. It’s also possible to develop it in-house.
3. Insurance
No matter how much you focus on compliance, processes and mitigating risks mistakes happen, and litigation follows. All businesses should have workers compensation and general liability insurance, but two other policies are particularly important for SaaS companies.
Tech Errors & Omissions
This policy, also known as a “professional liability insurance” policy, is designed to protect your company from lawsuits alleging negligence in your professional capacity. For a SaaS company, an example would be a lawsuit alleging that you failed to uphold your part of the contract (ex. not delivering the product suite promised in marketing materials or not hitting milestones) and causing customer lost income. Since a SaaS company is built on serving customers, this is one of the most critical policies your company needs to have.
Cyber Liability
If your customers can purchase your services over the web, then you likely hold enormous amounts of sensitive data such as financial information, SSNs and more. You are also required to comply with many privacy and notification laws regarding the loss of this information. A cyber policy is designed to protect you from the financial consequences of a cyber attack. The policy will pay for notification costs, damage to your systems and the cost to comply with regulations.
The cost of these policies varies considerably depending on the coverages that you purchase to cover the unique risks your organization faces. The most significant factor that affects your premium is the number of subscribers that you have. A cyber policy will also take into account your security measures to fend off a cyber attack.
Shop Around
Regardless of which insurance policy you are considering purchasing, by not shopping around you are likely leaving both money and more advantageous insurance terms on the table. Each insurance carrier has an area they specialize in, unique coverages that they may offer and some brokers may have access to exclusive programs not available anywhere else.
So while we do suggest looking around and comparing a few quotes, there is something to be said against approaching too many insurance brokers. All brokers have access to a pool of insurance carriers, but that number is finite, so ultimately you will encounter a situation where these brokers approach the same company for a quote. Work to find a trustworthy broker that knows your industry. After you’ve found the perfect broker for your business, let them do the tricky part of negotiating with carriers.
The risks are certainly large, but by implementing the above protocols and checks, you can keep user data safe and uptime consistent.