Key Takeaways
Cybersecurity was sleepless in 2025, as was cybercrime. Although ransomware remains the largest contributor to cyberattacks—44% of breaches analyzed by Verizon involved ransomware—AI-related crime is on the rise, with increasingly sophisticated social engineering and automated attacks taking place.
With threats looming from seemingly every corner, companies are responding with similar tactics, implementing AI to monitor, spot, and fight potential threats from the root. According to Cybersecurity Ventures, it’s the small entrepreneurs who must pay closer attention, as they were disproportionately targeted by hackers in 2025, making up around half of businesses attacked.
Let’s explore how these trends were reflected in the cyber insurance space, and what 2026 has in store for premium prices and suggested best practices.
Cyber Insurance Market Update
Whether due to cloud provider outages or direct cyber incidents, many companies in 2025 got a taste of the risks posed by vulnerable systems. For instance, the AWS outage in October generated 17 million user reports and left giants like Snapchat and Netflix stranded without service. This downtime doesn’t just involve operational damage, but also reputational damage across the board.
Cyber Security Trends of 2025
Ransomware remained the most dominant threat in 2025. Contingent business interruption (CBI) was the top financial driver due to losses from prolonged downtime, rather than just the ransom payment itself. Business email compromise (BEC) was a close second, with sophisticated, AI-enhanced social engineering leading to fund transfer fraud.
Moreover, the AWS outage case was just one of the several supply chain incidents that exacerbate systemic risk exposure, turning SaaS providers and managed service providers (MSPs) into new attack surfaces for companies hiring their solutions.
And, while not a direct consequence of cybersecurity threats, litigation due to user privacy breaches is on the rise. Cases involving the Video Privacy Protection Act (VPPA) are increasing due to websites adopting pixel tracking, which exposes users’ browsing activity, enhancing the number of cyber insurance claims on this front.
AI also continues to grow as a double-edged sword that simultaneously attacks and defends systems. On one hand, hackers are launching highly personalized phishing and deepfake attacks at a massive scale, making even the most trained eye fall for online scams.
On the other hand, companies are leveraging AI to fight fire with fire, using the technology to catch attacks before they happen—insurers increasingly reward firms that use AI and endpoint detection response (EDR) for real-time threat detection and mitigation. In fact, it’s these practices driven by faster identification and containment that led to a 9% decrease in data breach costs compared to 2024, as reported by IBM.
For insurance premiums, these quick tech developments have meant that 2025 began with 39% of accounts increasing their price at renewal, slowly descending to 27% by Q3, while the amount of decreasing renewals grew from 33% to 44%.
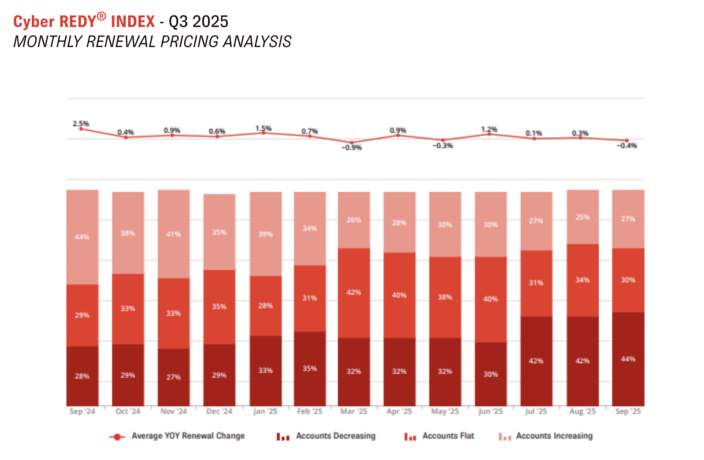
Source: Cyber REDY Index Q3 2025 | CRC Group
Industries with the Most Cyber Attacks
In 2025, the global cybersecurity landscape reached a critical inflection point. The year was defined by a transition from traditional “hacking in” to sophisticated “logging in,” as threat actors leveraged AI to automate credential harvesting and conduct hyper-personalized social engineering at scale. Manufacturing remained the most targeted sector due to the high-stakes pressure of industrial downtime, while the healthcare and education sectors saw record-breaking ransom demands as attackers exploited their essential services and under-resourced defenses.
Based on cybersecurity data and breach reports from 2025, the following sectors were the primary targets for threat actors:
- Manufacturing
- Education
- Healthcare
- Finance & Insurance
- Government & Public Sector
- Professional & Business Services
- Energy & Utilities
- Telecommunications
- Technology & SaaS Providers
- Retail & E-Commerce
- Transportation & Logistics
- Hospitality
How Cyber Liability Benefits All-Sized Companies
By now, we’ve seen that, whether large or small, all-sized companies are affected by the current threat landscape, laden with the side effects of geopolitical conflicts, tech advancements, and overall weak cyber practices. In turn, cyber liability has become an essential part of a company’s risk management strategy, providing respite in the aftermath of incidents.
To better understand the large scope of cyber liability coverage, let’s look at some real-world examples of common cyberattacks that unfolded this past year, and which surely triggered claims in their policies.
Cyber Risk Management Guide
The Largest Crypto Hack in History
In February 2025, North Korean hackers performed what is now known as the biggest cryptocurrency heist in history, attacking the Dubai-based crypto exchange platform ByBit. The hackers extracted a total of $1.5 billion in Ethereum tokens—$160 million of which were laundered shortly after—hurting the global crypto market and urging lawmakers worldwide to enact stricter crypto regulation.
Unfortunately, experts deem cryptocurrency as a moving target for law enforcement as threats increase in tandem with its growing community, often becoming a hotbed for money laundering.
Leading Airlines Targeted as Customer Data Goldmines
In late June, the FBI issued a warning to the public, declaring that major airlines were possibly being targeted by hacking group Scattered Spider, believed to be based between the US and the UK.
It all started when Australian airline Qantas reported a breach to a third-party customer center that left customers’ information exposed, followed by Canadian airline WestJet having its internal systems and WestJet app hacked, and finally Hawaiian Airline’s claiming its IT systems had been compromised.
The nature of these attacks wasn’t explicitly financially driven, but rather to gain personal data that could be then sold on the dark web or exploited for financial gain. Although the three airlines continued their operations, customers were told to stay alert to possible breach attempts by authorities, and to “assume they’re affected” by the cybersecurity company McAfee.
Zero-Day Vulnerability Exposes Software Giant
In September, Google Threat Intelligence Group (GTIG) reported that cloud services provider Oracle had been the victim of an extortion campaign by Clop, a known extortion brand. The hackers exploited a zero-day vulnerability in the company’s E-Business Suite (EBS) environments, allegedly taking sensitive customer data.
Although Oracle had already released a patch update for its suite, it released a new emergency patch following the report of Clop’s breach. According to GTIG, the attack began even before the first patch was available, stealthily penetrating customer environments until reaching the zero-day vulnerability.
Cyber Insurance Outlook for 2026
It’s nothing new for insurers to place careful consideration on your cybersecurity practices to give you the best coverage and premium. However, with the latest developments, they’re scrutinizing specific practices even more, ensuring governance, response plans, and updated technology are being enforced in your business.
Market Cycle Forecast
Companies with clean records and apt practices will continue seeing stable premiums as the market softens toward decreasing prices. Evidently, this won’t apply to businesses that haven’t adapted their cyber practices to today’s strict standards, which are, rather than a whim, a vital part of a company’s operations.
The AI Litigation Wave
Although ransomware attacks are bound to continue, the legal focus will be shifting to AI-related incidents, whether that’s bias, malfunctioning, or IP concerns, resulting in errors and omissions (E&O) and privacy claims.
Mandatory Security Evolution
Before shopping for new insurance or contacting your broker to renew your policy, ensure your cyber hygiene is up to date with current security needs—the new minimum includes adopting phishing-resistant multi-factor authentication (MFA) such as FIDO2 security keys.
When underwriting, the focus will be on showing proof of tested incident response plans and third-party vendor audits.
Regulatory Enforcement
Claims stemming from regulatory fines and directors’ liability from reporting failures aren’t declining anytime soon. This is why compliance with the Securities and Exchange Commission (SEC) regulations and the Digital Operational Resilience Act (DORA) in the EU will be paramount to gain the insurance higher ground.
Key Cyber Risk Mitigation Trends Shaping 2026
It has never been more critical to closely monitor the cybersecurity space and adjust company practices accordingly. This is, in fact, the final step of an outstanding risk management strategy that spots weaknesses, solves the issue, and continues looking for improvements. To follow up on a year filled with ingenious and elaborate attacks, here are some practices you should adopt to polish your risk mitigation plan.
Identity Protection: Moving Beyond Basic MFA
Traditional MFA, such as SMS or simple push notifications, might’ve done the trick in years past. However, they won’t fly going into 2026 with the rising wave of Adversary-in-the-Middle (AiTM) phishing attacks. This has led insurers to require Phishing-Resistant MFA (PR-MFA) for privileged, executive, and remote access. Full adoption of Zero Trust Architecture (ZTA), which continuously verifies users and devices rather than just the perimeter, will also gain more traction in the coming year.
We see PR-MF becoming the preferred, if not mandatory, control for high-risk users and critical systems. This means adopting stronger methods, like FIDO2 security keys or advanced, number-matching authentication apps that prevent Adversary-in-the-Middle (AiTM) attacks.
Data Resilience and Recovery Focus
Ransomware attacks are also evolving to become even more aggressive. For instance, we’ve seen a rise in double extortion, with hackers not only encrypting data but also threatening to publish it. This is why immutable backups—ensuring backup data cannot be altered, deleted, or encrypted by a ransomware strain, regardless of network access—are becoming the standard in best cybersecurity practices.
The biggest ransomware impact, business interruption (BI), is creating a new trend of building comprehensive Business Continuity and Disaster Recovery (BCDR) plans. On top of this, they must be tested quarterly to minimize BI losses, which are the highest cost component of a cyber claim.
This is when micro-segmentation also becomes essential: Networks should be actively divided to isolate critical assets, such as finance servers or backups, from the general network. The goal is to contain the blast radius or any intrusions, although defense strategies should begin to emphasize minimizing downtime and BI rather than simply preventing incidents.
Proactive Endpoint and Network Defense
The rising use of generative AI by attackers to launch automated, sophisticated malware campaigns is leading to a more ubiquitous deployment of Endpoint Detection and Response (EDR). Additionally, companies are going a step further by implementing Extended Detection and Response (XDR) for all devices, coupled with a round-the-clock Security Operations Center (SOC) or Managed Detection and Response (MDR) service.
These new practices are leading to a prioritization of Vulnerability and Patch Management (VPM), especially for internet-facing edge services such as VPNs and firewalls. Overall, and in the wake of the Oracle Clop extortion case, we expect this type of continuous management to keep trending in the new year.
Third-Party and Supply Chain Governance (TPRM)
As noted by the WestJet data exploit, among many other data breach cases in 2025, third-party vendor incidents are becoming a major systemic risk—we’ve noticed that they often account for over 30% of major claims.
As a result, formal Third-Party Risk Management (TPRM) programs will become a requirement rather than a nice-to-have. We believe that TPRM will shift from periodic assessments to continuous monitoring, and the “once-a-year questionnaire” approach to vetting vendors will be rendered obsolete.
Furthermore, insurers will demand evidence of contractual safeguards, like vendor contracts stipulating security standards, audit rights, and timely breach notification.
Governance and Human Element Controls
The easiest way to penetrate systems is still the human element by way of phishing attacks. This is why we can’t stress enough the importance of increased investment in security awareness training, which should include simulated phishing drills and a higher focus on high-risk employees (executives, finance team, governance department, etc).
This importance placed at the top means underwriters are increasingly asking for proof of board and executive-level involvement in cyber risk oversight, treating cybersecurity as a strategic function rather than an IT task.
To conclude, the quick development of AI tech is leading organizations to be required to demonstrate AI governance frameworks for both internally developed and third-party AI tools.
Saying that the cybersecurity landscape has become more aggressive as the years pass shouldn’t be surprising to anyone. What we expect from the space is the same concern for their systems, evolving with the threats that adhere to tech advancements. This isn’t to say cybersecurity is becoming a steep climb where you can never reach the top, but rather a growing aspect of your business that requires constant nurturing. With this in mind, your level of protection should mimic new trends, ensuring that your company can thrive by adopting emerging technologies and advanced industry practices while averting potential cyber incidents.









